Infospotlights delivers comprehensive server security solutions designed to protect critical workloads, applications, and data across on-premises, cloud, and hybrid infrastructures. Our server security framework focuses on hardening, monitoring, access control, and continuous defense to ensure maximum uptime, integrity, and resilience.
Services Include:
Hardened and secure Windows, Linux, and cloud servers
CIS, ISM, and Essential Eight–aligned configurations
EDR/XDR workload protection with real-time threat defense
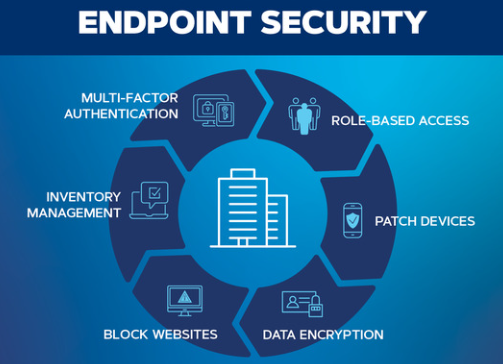
Strong access control with MFA, RBAC, PAM/PIM
Continuous monitoring through SIEM, logs, and analytics
Vulnerability management and rapid patching
Compliance-ready controls for ISO 27001, SOC2, PCI-DSS
Secure operations across on-prem, cloud, and hybrid environments